HIPAA compliance… it’s a big deal in the US healthcare scene — like, really big. At ScriberJoy, we’ve got our heads wrapped around the tangled mess of rules and hurdles that organizations have to jump through just to keep up with these tough-as-nails regulations.
Our recent — and eye-opening — HIPAA compliance survey? Turns out, a bunch of healthcare providers are still scratching their heads, trying to nail down and roll out all the steps they need. So, let’s break it down for you. This blog post is your handy guide through the maze of HIPAA compliance, with real, actionable steps to make sure your organization is hitting all the right notes.
What Is HIPAA and Why Does It Matter?
The Essence of HIPAA
HIPAA, or the Health Insurance Portability and Accountability Act… it’s the MVP of patient privacy in the U.S. Congress, back in ’96, rolled out this federal law to lock down sensitive patient data. But hold on-HIPAA isn’t just about putting medical records under lock and key; it’s the rulebook for how healthcare providers, insurers, and their business pals play ball with every piece of health info they touch.
The Three Pillars of HIPAA
This thing stands on three big rules-think of ’em like the three legs of a stool: Privacy, Security, Breach Notification.
- The Privacy Rule? It’s all about who gets to see your info. It puts the power in the patients’ hands, letting them say who gets a peek at their health details.
- The Security Rule is the bouncer at the ePHI club. Organizations must arm themselves with some top-notch digital defenses to fend off the cyber boogeymen and any unauthorized eyes.
- And when the unthinkable happens-the Breach Notification Rule steps in. It’s the fire alarm… covered entities and their business associates must alert patients, the government, and the media (sometimes) when data spills out.
Who Must Comply with HIPAA?
HIPAA’s got its arms wide open in the healthcare world. It’s not just about doctors-nope, covered entities are:
- Health plans
- Healthcare providers
- Healthcare clearinghouses
Plus, it’s not just about them. Business associates-think IT support, billing outfits, or cloud storage guys handling PHI for those covered entities-are in the mix too. The Security Rule wields a national rulebook to shield health info that’s zipping around electronically.
The Stakes of Compliance
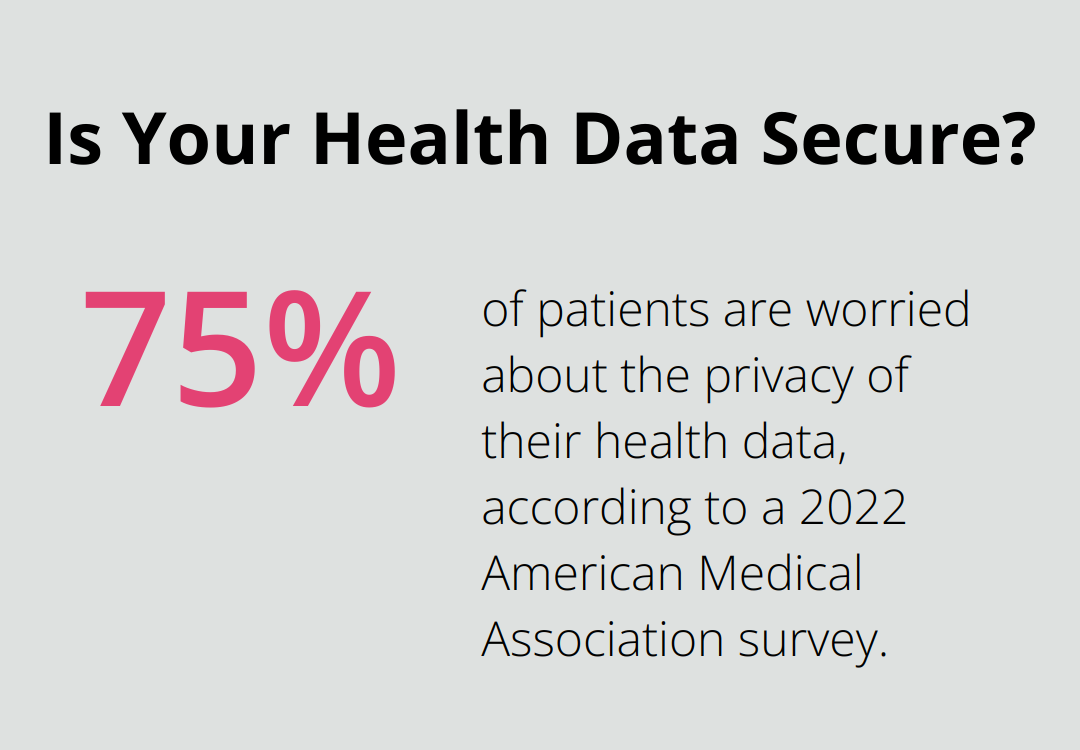
HIPAA compliance… it’s more than dodging those sky-high fines (up to $1.5 million per violation type each year). It’s about building trust, showing patients you’ve got their backs with their most personal details. A 2022 American Medical Association survey popped the lid on this-75% of patients are biting their nails over the privacy of their health data. Healthcare outfits that follow HIPAA like it’s gospel, step up to the plate-addressing those worries, showing they’re all about patient privacy.
Moving ahead, just getting your head around HIPAA’s rules? That’s only the first base. The real game is nailing down these regs in your organization. Let’s dig into the DNA of a rock-solid HIPAA compliance program.
HIPAA Compliance Essentials (aka Trying to Keep Your Medical Data on Lock)
The Privacy Rule: Protecting Patient Information… for Real
The Privacy Rule – think of it as the backbone of HIPAA – sets the game plan for keeping your medical records under wraps. It’s not just a suggestion paper; it demands healthcare folks to roll out hardcore policies to keep your data off the black market. We’re talking about limiting what info gets shared – and only doing it when there’s a legit reason.

Key player here? The Notice of Privacy Practices. Yeah, the paperwork everyone loves to ignore but shouldn’t. This little number lets you know the scoop on how your info could be tossed around. Why do we care? Because it’s about earning patient trust and shouting, “Hey, we’re serious about your privacy.”
The Security Rule: Beefing Up Your Digital Fort Knox
In this ever-spinning cyber galaxy, the Security Rule is like… the superhero swooping in. It’s not just about dusty firewalls – it’s a full-blown cybersecurity regime. “Secure everything” means regular threat sweeps, setting up gatekeepers (access controls), and covering data with an encryption blanket, whether it’s chilling in files or zooming through the internet.
Breach Notification: The “Oops, We Goofed” Protocol
Even with all that armor, data breaches sneak in like ninjas. The Breach Notification Rule is your crisis playbook when unsecured PHI gets exposed to the wrong eyes. When the inevitable happens – bam, 60 days to alert the affected folks, tell the Health and Human Services honchos, and sometimes even air it out to the media.
Why bother? It’s about owning up and acting fast – reducing damage and keeping the trust bond with patients strong and sturdy.
Patient Rights: Giving Power to the People (aka You)
HIPAA isn’t just about shackling providers with rules. It’s also your buddy, giving you a suite of rights. Picture this – you can peek at your health records, hit up corrections, see who’s been checking out your data, and even say, “Hey, maybe don’t share this info, please?”
Turning these rights into reality isn’t just about ticking boxes. It calls for a cultural revolution, putting patients in the driver’s seat. When done right, it leads to patients singing praises and feeling more connected.
As we chart the way forward, we’ll dive into how organizations can nail HIPAA compliance and keep it rock-solid. These basic moves lay the groundwork, but the real world? That’s where the magic – and the mess – happens.
How to Achieve HIPAA Compliance
Risk Assessment: Your Compliance Compass
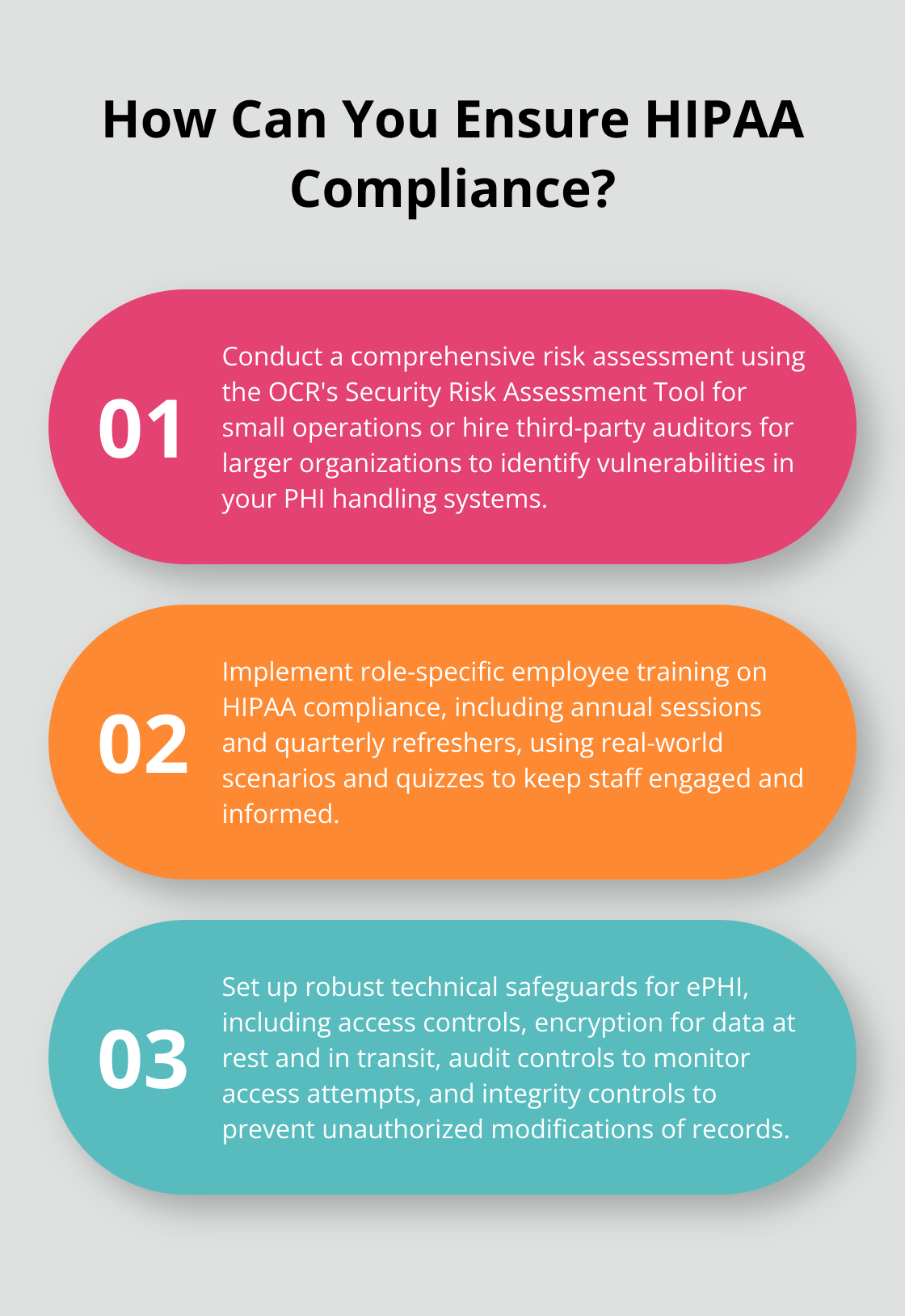
Jumping into HIPAA compliance is like crafting a strategy to defend a castle. Start with a comprehensive risk assessment-your trusty map. This process exposes every nook and cranny where your system might be leaking protected health information (PHI). The goal? Stop data breaches before they throw a party.

Picture this: PHI tucked into electronic health records, physical files, and-yes-even that relic of a fax machine in the corner. Once you’ve mapped it all out, dive into the ‘What if?’ game. What’s lurking as a potential risk? How likely are those risks to crash your castle? And if they do, what’s the damage?
For smaller operations, the Office for Civil Rights (OCR) hands you a Security Risk Assessment Tool on a silver platter. Bigger fish? Go big-third-party auditors can pinpoint those sneaky vulnerabilities you might miss.
Policies and Procedures: Your Compliance Playbook
Now, armed with your risk assessment, craft a set of policies and procedures to guard your kingdom. This is your compliance playbook-think of it as the unwritten rules of dodgeball.
Grab templates from the Department of Health and Human Services (HHS) as your baseline. Tailor them to your world-covering the essentials like access control, data encryption, incident response, and how you’ll tackle breach notifications.
(Pro tip: Roping in your team to shape these rules? Pure gold. They’re on the frontlines; they know the real deal.)
Employee Training: Your First Line of Defense
Your crew-frontline soldiers in this compliance battle. Equip them with the knowledge arsenal they need. Comprehensive training is your secret weapon.
Minimum order of business: annual training. But why stop there? Throw in quarterly refreshers to keep HIPAA front and center. Use juicy tidbits-real-world scenarios, quizzes, even some phishing attempts-to keep everyone on their toes.
Make it relevant-different strokes for different folks. IT needs a different playbook than the front desk. Train according to role risk because-and you can bet money on this-one-size-fits-all never fits anyone.
(Remember: Log it all. Attendees, dates, content. It’s your knight in shining armor when audits come knocking.)
Technical Safeguards: Fortifying Your Digital Defenses
When it comes to electronic PHI (ePHI)-build those walls tall and defenses mighty. Here’s your to-do list:
- Access Controls: Only the knights with credentials get in.
- Encryption: Lock down data whether it’s resting or taking a Sunday drive.
- Audit Controls: Keep your eye on who’s trying to peek behind the curtain.
- Integrity Controls: Ensure no one’s secretly scribbling on or torching your records.
Consistent system updates and patches? Non-negotiable. Automate them where you can. Consider it setting and forgetting-but with the peace of mind that you’re protected.
Business Associate Agreements: Extending Your Compliance Shield
Working with vendors handling PHI? Gotta lock down those Business Associate Agreements-the ring that binds them to play nice and follow HIPAA rules.
Stay on top of those contracts. As your Rolodex evolves, so should your BAAs. A proactive stance keeps compliance running through your whole network of allies. Because when they’re connected, you’re protected.
Final Thoughts
HIPAA compliance-it’s the backbone of healthcare ops in the U.S. It keeps patient info secure, builds trust like a cornerstone, and boosts an organization’s street cred. But… our recent HIPAA compliance survey shows healthcare providers are still wrestling with it like an octopus on roller skates. Messing up on compliance? That’s a one-way ticket to financial doom and maybe even a cell with bars.
Staying HIPAA-compliant-it’s like running a marathon you never actually finish. You’ve got to keep working at it. The Department of Health and Human Services (a bureaucratic behemoth) throws lifelines-guidance and tools-to help manage this never-ending journey. Plus, there are professional groups and consultant ninjas with healthcare compliance superpowers that offer tailored tips and tricks. (These are golden when you’re wading through the HIPAA quagmire.)
At ScriberJoy, we totally get why HIPAA compliance is critical in the world of healthcare documentation. Our secret weapon? Medical transcription software that helps healthcare pros keep their HIPAA creds while nailing their documentation game. We’re all about harnessing AI magic with a human touch for top-notch accuracy in medical transcriptions, and yes, we stick like glue to tough HIPAA standards.

Leave a Reply
You must be logged in to post a comment.