HIPAA compliance—it’s crucial for healthcare data security, no question. At ScriberJoy, we get it. Keeping sensitive patient info under lock and key? Not just important—it’s a must.
Here’s the deal: Conducting a thorough risk analysis for HIPAA compliance isn’t optional. Healthcare organizations need to step up and pinpoint those potential weak spots. This guide? It’s your roadmap—practical steps, valuable resources. Your mission: safeguard your patients’ data. Period.
What Is HIPAA Risk Analysis?
Defining HIPAA Risk Analysis
HIPAA risk analysis – it’s a big deal in healthcare. Why? Because it’s all about hunting down threats to that sacred electronic protected health information (ePHI). Not just another tick-the-box gig-it’s a deep dive into your whole data universe.
At its heart, HIPAA risk analysis is a full-blown risk assessment. We’re talking scouring for any weak spots in how you manage patient data. Everything’s on the table-from your electronic health record system to Bob’s casual email habits. The endgame? Catch those vulnerabilities before they snowball into major breaches.
The Department of Health and Human Services (HHS) says a solid risk analysis should size up how likely and impactful potential ePHI risks might be. And newsflash-it’s no “one-size-fits-all” deal. You’ve gotta tailor this bad boy to fit your specific turf.
Key Elements of Risk Analysis
So, when you’re diving into this risk analysis thing, focus on these pivotal pieces:
- Scope of the analysis: Pin down every bit of ePHI you’ve got, no matter where it’s chilling.
- Data collection: Round up details about ePHI-where it’s hanging out, how it gets there, and what’s maintaining it.
- Threat identification: Line up all possible human, environmental, and natural threats targeting ePHI systems.
- Vulnerability identification: Sniff out the weak points that could get exploited.
- Security measures assessment: Size up the security shields you’ve already got in place for ePHI.
The Importance of Regular Assessments
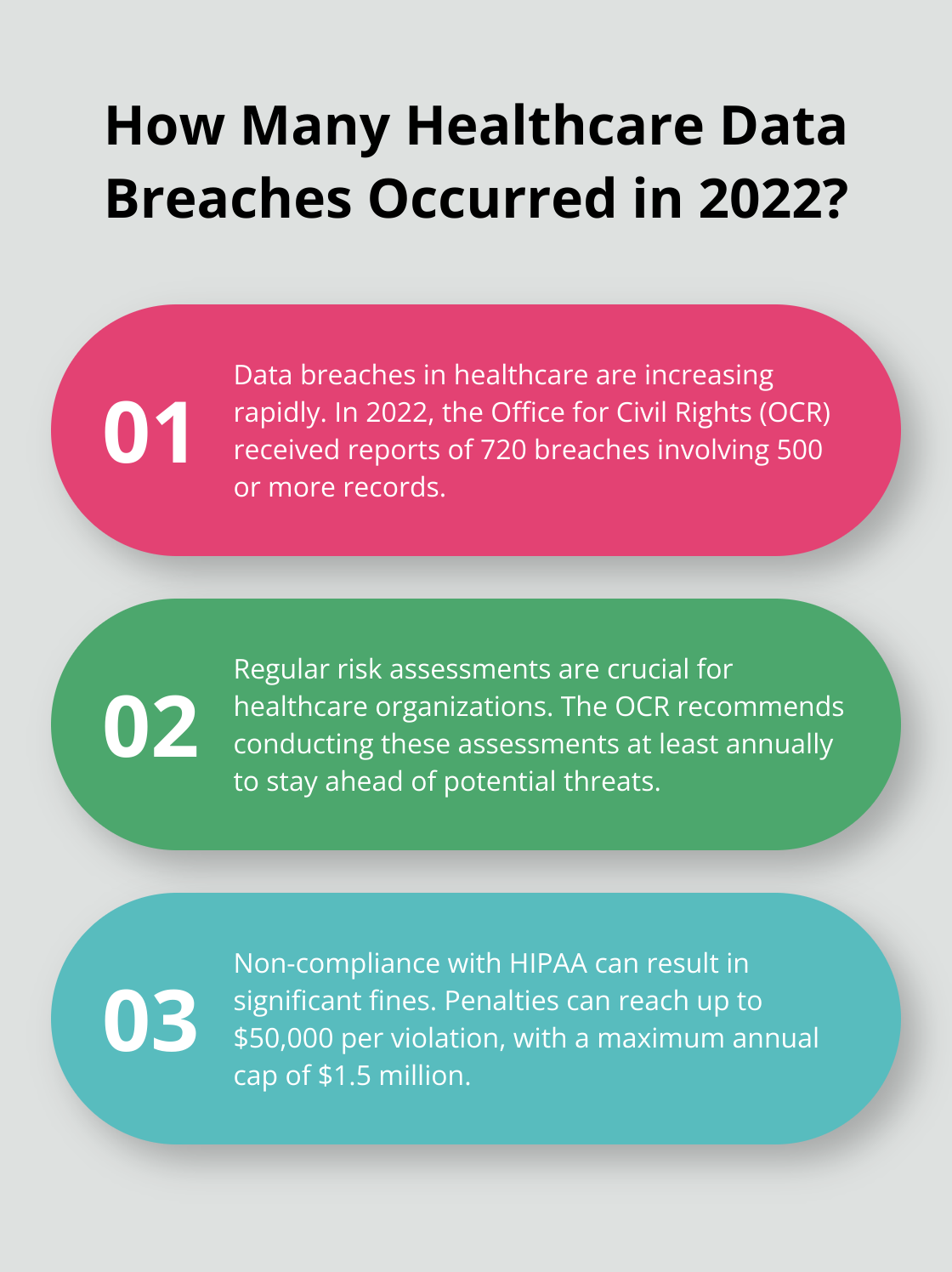
Data breaches in healthcare – they’re skyrocketing. Data breaches spiked in 2022, with OCR getting hit with reports of 720 breaches involving 500 or more records. Just more proof why regular risk check-ups aren’t just a nice-to-have-they’re downright critical.
Making these risk assessments an annual ritual, at the very least, keeps you one step ahead of the predators. As your organization morphs and shifts, so do your vulnerabilities. New tech, people coming and going, and those ever-changing rules-it all messes with your risk landscape.
Plus, the Office for Civil Rights (OCR) says do these at least yearly. Non-compliance fines? They can hit $50,000 per slip-up (with a whopping $1.5 million cap per year). That’s a fat bill to pay just for dodging a task that should sit pretty in your standard operating playbook.
Preparing for Your Risk Analysis
Before charging into your risk analysis, prep time is key. Seriously overlooked, but if you want the analysis to actually work, don’t skip this. Here’s how:
- Assemble your team: Loop in IT gurus, compliance ninjas, and department chiefs.
- Gather documentation: Snag those policies, procedures, and any past life risk assessments.
- Map your data flow: Lay out the journey of ePHI through your whole operation.
- Set a timeline: Nail down deadlines for each segment of the analysis.
Got a grip on what HIPAA risk analysis is all about? Armed with these prep essentials, you’re ready to dive elbow-deep into the actual nitty-gritty of the analysis. Stay tuned-let’s break down those steps in detail next.
How to Conduct a HIPAA Risk Analysis
Map Your ePHI Landscape
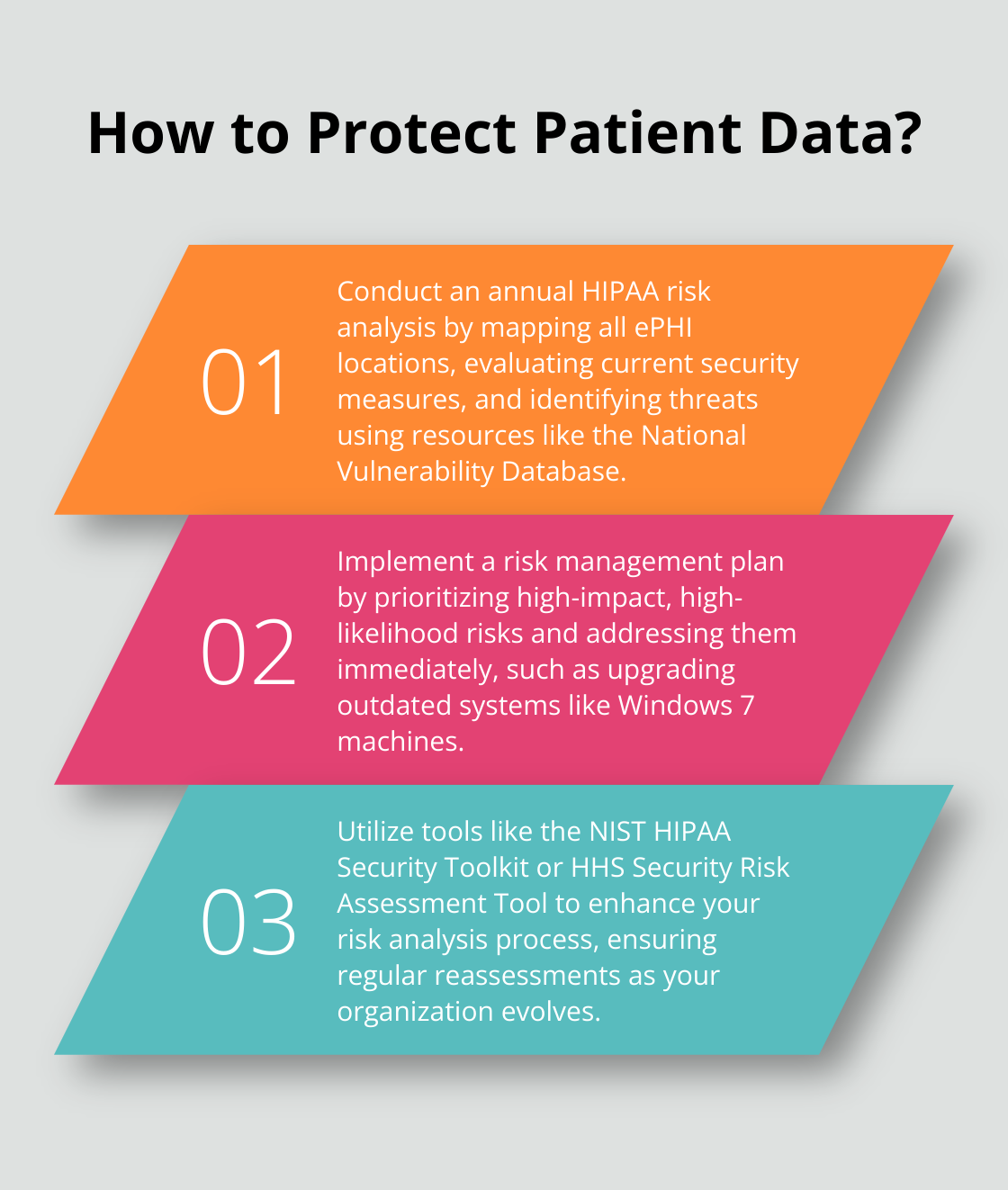
Step one – find every nook and cranny where your electronic protected health information (ePHI) might be chilling. Time for a full roll call of every system, app, and gadget that touches ePHI. And yes, even the dusty old servers or whatever cloud service your team swore they’d ditch last year… include those.

Here’s a little cheat code: whip out data flow diagrams. Mapping out how ePHI moves through your organization might just spotlight surprise connections and weak links you never knew existed.
Evaluate Your Current Defenses
Once you’ve got the lay of the land, it’s time to judge your current security setup. Check out everything – we’re talking password policies to physical security measures.
Be brutally honest here… if you’re falling short, better to know now. Even if healthcare cybersecurity incidents dropped by 8% in February 2022, there were still 46 hiccups. Skip the stats club and fix things before they break. Healthcare cybersecurity incidents.
Identify Threats and Vulnerabilities
Next step – figure out what’s lurking out there and what’s dodgy inside your ePHI. Yeah, it’s about those external threats like hackers and malware, but sometimes Janice from accounting clicking a sketchy link is just as risky.
Stay sharp with threat intelligence feeds and vulnerability scanners. Lean on resources like the National Vulnerability Database (NVD) to keep tabs on the threats in your tech neighborhood.
Assess Risk Levels
Now that you’ve got the bad guys – and their favorite loopholes – pegged, it’s time to weigh up each risk. No room for guesstimates here, folks; let’s get systematic.
Construct a risk matrix that pits likelihood against impact. The double-threats? High-likelihood, high-impact should be numero uno. Got machines still running Windows 7 (a too common ghost in healthcare)? Ding, ding – that’s high priority… fix ASAP.
Craft Your Risk Management Plan
Time for the battle plan. Use your risk assessment data to wage war. Rank those risks and lay out clear-cut strategies to combat each one. This could mean tech upgrades or maybe shuffling your operations deck with new training regimes.
Stay realistic – like, don’t bite off more than you can chew. Tackle high-priority gremlins head-on, then trickle down the list.
Remember, a risk management plan isn’t a “set it and forget it.” Keep your eyes peeled; vigilance is key. Regular reassessments are your new best friend. Pencil in a schedule to review and update your plan – go for at least annual, but if your org’s doing the transformation tango, you might want to up that frequency.
These steps? They’re like the secret sauce for cooking up a solid thorough risk assessment in the HIPAA compliance kitchen. It’s no walk in the park, but hey, keeping patient info safe is what it’s all about. Stick around for the next segment, where we dive into the tools and resources that can give your HIPAA risk analysis a serious boost.
Tools to Enhance Your HIPAA Risk Analysis
HIPAA risk analysis isn’t a solo mission. You’ve got some solid tools at your disposal to make compliance less of a headache. Let’s dive into some key resources to pump up your HIPAA compliance strategy.
NIST HIPAA Security Toolkit
Enter the National Institute of Standards and Technology (NIST) with its powerhouse HIPAA Security Toolkit. It’s the Swiss Army knife for healthcare outfits looking to beef up their security game.
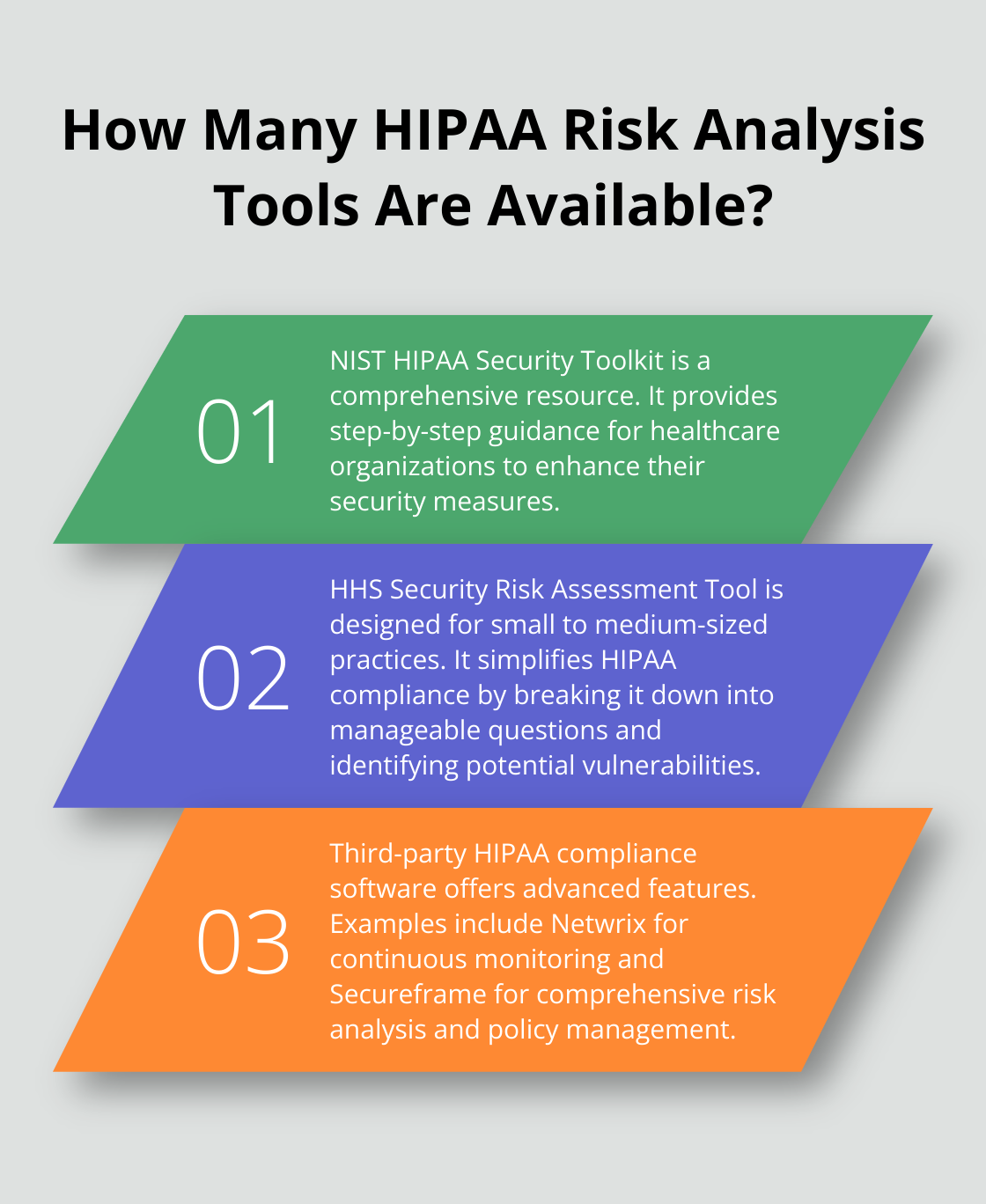
The toolkit’s like a GPS for the HIPAA Security Rule. It walks you through – step by step – everything you need. Stick with it, and you’ll walk away knowing what’s working and what needs some serious TLC.
And, here’s the kicker – don’t just give it a whirl once and call it a day. Make it a regular thing. As your organization grows and pivots, your security measures should keep pace.
HHS Security Risk Assessment Tool
Next up, the Department of Health and Human Services (HHS) rolls out the Security Risk Assessment Tool. Tailor-made for small- to medium-sized health practices (think 1 to 10 providers) and the entities they cover.
Why’s it a standout? Ease of use, folks. This thing turns the tangled mess of HIPAA into bite-sized, digestible pieces. You just answer questions about your setup, and voilà – potential pitfalls, served up on a silver platter.
Remember though, this tool’s like a wise old sage – it offers wisdom but won’t make you compliant on its own. Use its insights to plug those gaps, then roll up your sleeves and get to work.
Third-Party HIPAA Compliance Software
If you’re all about going big, third-party HIPAA compliance software is the way to go. These tools bring the heavy artillery to your risk analysis and management plan.
Take Netwrix, a tool that’s got your back with risk assessment and non-stop system monitoring. It’s like having a security guard on duty 24/7, ready to pounce on any threat.
Secureframe puts everything under one roof – from risk analysis to policy management. It’s all in there, streamlined for your convenience.
But let’s keep it real, these tools – despite their power – aren’t magic bullets. They need your input to really shine. Implement their advice and keep those security defenses tight.
Choosing the Right Tool
Pick what fits your organization’s vibe. Whether you’re rolling with a freebie from the government or shelling out for a third-party powerhouse, the secret to winning the compliance game is consistency.
And if you’re searching for that sweet spot where precision meets productivity, ScribeJoy’s got your back. Our medical transcription software doesn’t just check the HIPAA compliance box; it also frees up your schedule by streamlining documentation, so you can focus on what truly matters – patient care.
Final Thoughts
HIPAA compliance and risk analysis… sounds like a dentist’s visit? Not quite, but just as critical for keeping patient data safe and your organization-intact. Here’s the deal: you’re mapping ePHI (yep, electronic Protected Health Information), checking out your defenses, spotting the gremlins (threats), gauging the risks, and whipping up a management plan. It’s the secret sauce for a rock-solid HIPAA strategy.
Now, buckle up-healthcare’s like a roller coaster. New tech, new threats popping up like mushrooms after rain. Keep your risk analysis fresh-minimum annual check-ups-but hey, here’s a tip: do it more often as you grow or tack on new systems.
The payoff? You boost patient trust, your operations get slicker, and ScribeJoy is in your corner with a HIPAA-compliant transcription solution. Accurate docs, less wasted time… and it blends into your workflows like coffee in your morning-keeping data safe and your processes smooth.

Leave a Reply
You must be logged in to post a comment.