HIPAA compliance… yeah, that’s a big one for software developers in the healthcare space. At ScriberJoy, we totally get it—the fine dance of juggling these regulations while still firing up some cool healthcare solutions (without getting slammed with fines or penalties).
Check this out: a HIPAA compliance checklist—a must-have for software development. Think of it as your playbook for hitting all the essential requirements and best practices. We’re talking about keeping your apps wrapped in tight security blankets, respecting privacy like it’s your grandma, and all while plotting ongoing compliance strategies that scream “trust me” to healthcare providers and patients. Basically, it’s like bringing a safety net to the healthcare tech circus.
What Are the HIPAA Requirements for Software Developers?
HIPAA-it’s like the rulebook for healthcare developers. Revolutionizes the game. It’s more than rules; it’s the fortress of patient data protection in our digital universe.
The Three Pillars of HIPAA
HIPAA stands tall on three big rules:
- The Privacy Rule: We’re talking fort Knox for patient records and personal health info. This is about shielding their data-keeping it in the vault unless the gatekeeper says otherwise. Developers working on eHealth apps (that might play with PHI) have to dance to this tune.
- The Security Rule: Now, this one is all about electronic protected health information, or ePHI-geek alert. Think of it as the bouncer at the club. Requires tight administrative, physical, and technical security checks to ensure ePHI doesn’t slip out the back door.
- The Breach Notification Rule: You mess up? You gotta fess up. This says HIPAA-covered entities and their associates must notify folks when unsecured protected info gets breached. Get the word out-to affected individuals, the Secretary, maybe even the media.
Essential Requirements for Software Developers
For developers-HIPAA compliance isn’t a suggestion. Here’s your checklist:
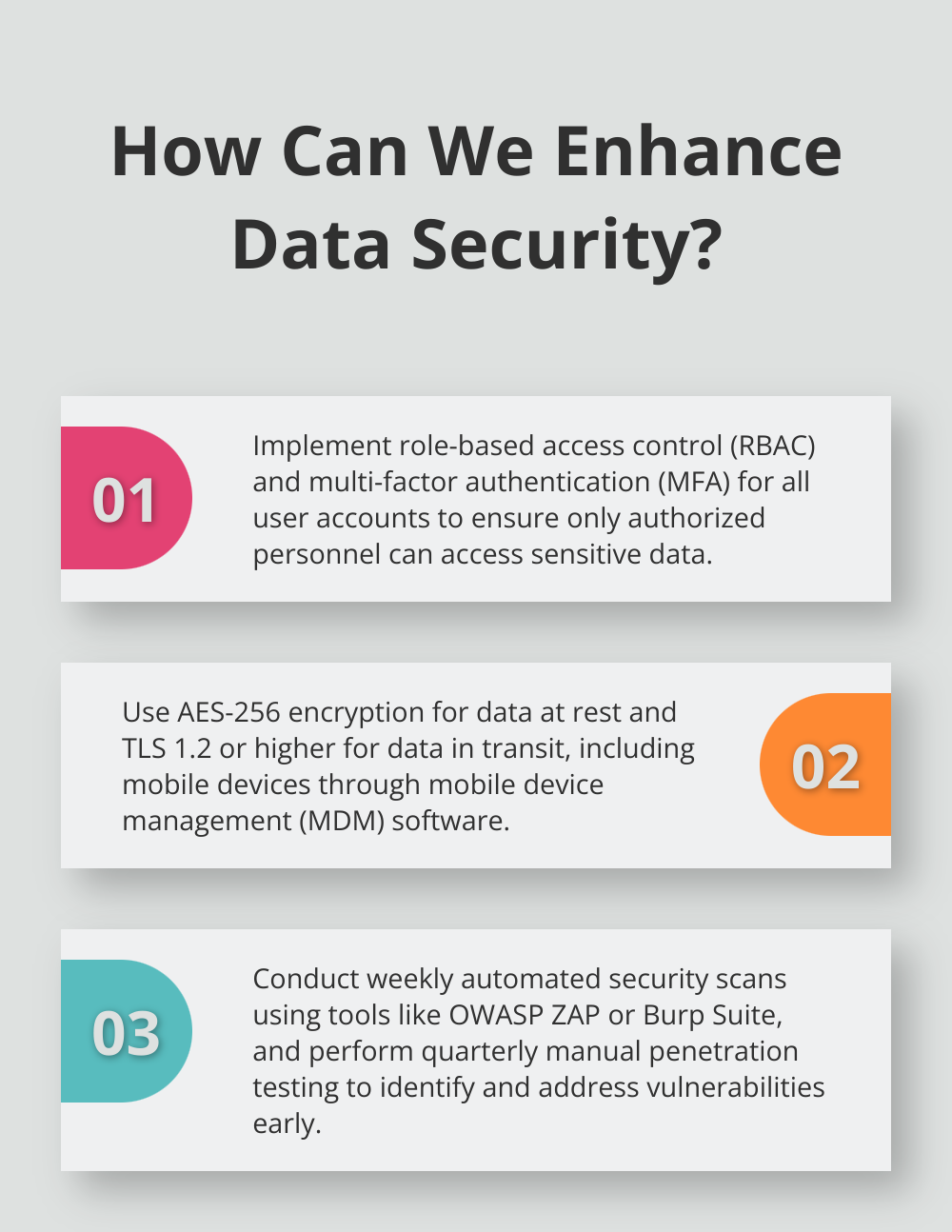
- Access Controls: Your software needs to be the Fort Knox of user access. We’re talking multi-factor authentication, role-based access, and auto sign-off if someone leaves the wheel unattended.
- Encryption: Data has to stay in stealth mode, whether it’s chilling or on the move. PHI needs encryption with at least 128-bit Advanced Encryption Standard. No easy peeks.
- Audit Trails: Keep a diary. Log all user activity-access attempts, data changes, system hiccups. These logs? Tamper-proof and ready for scrutiny.
- Data Backup and Recovery: Regular, secure backup drills and a bulletproof disaster plan are a must. Security Rule says: Keep exact ePHI copies handy.
- Secure Communication: All chat and file swap needs a heavy-duty, encrypted channel. No secret whispers here.
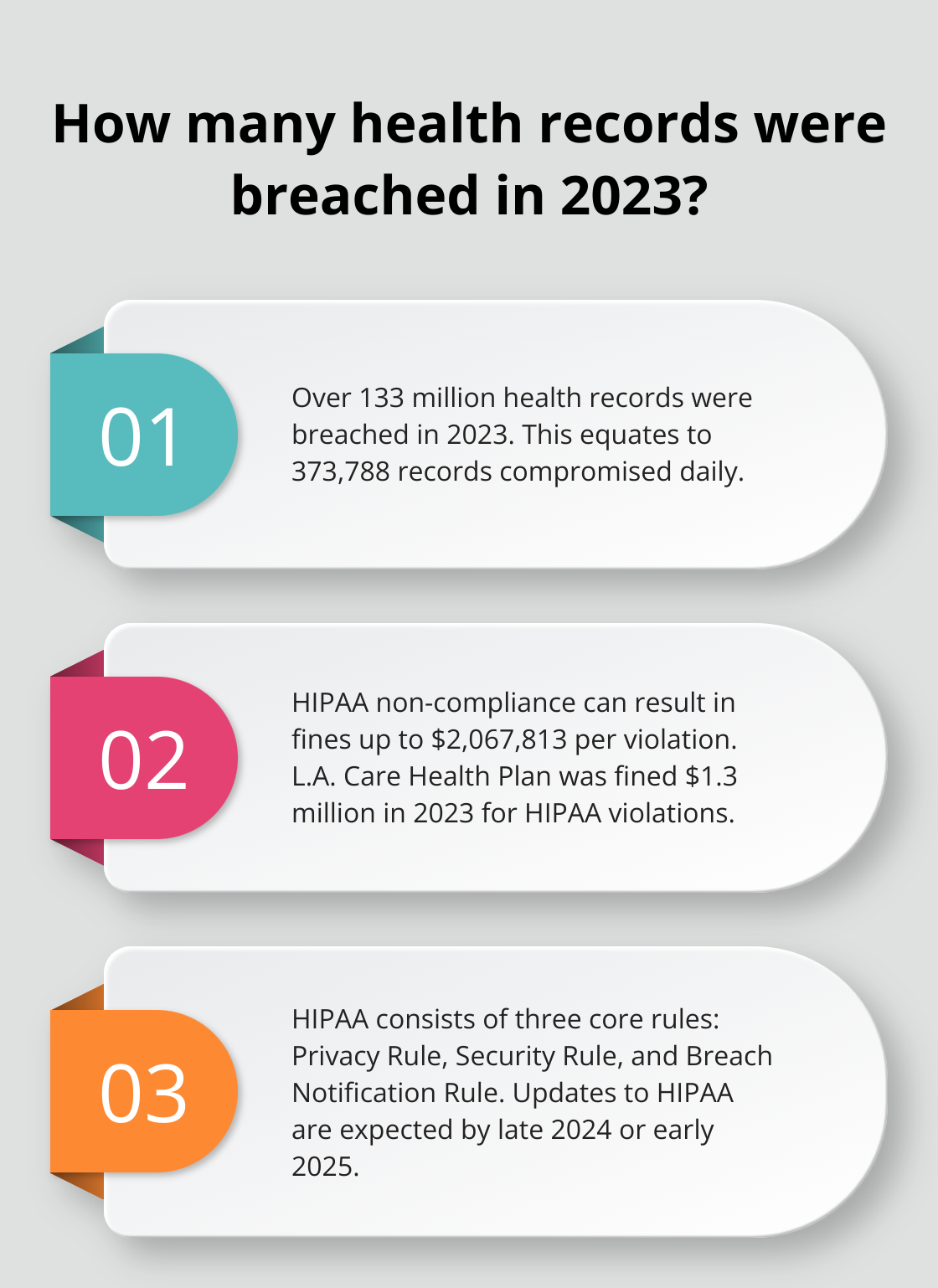
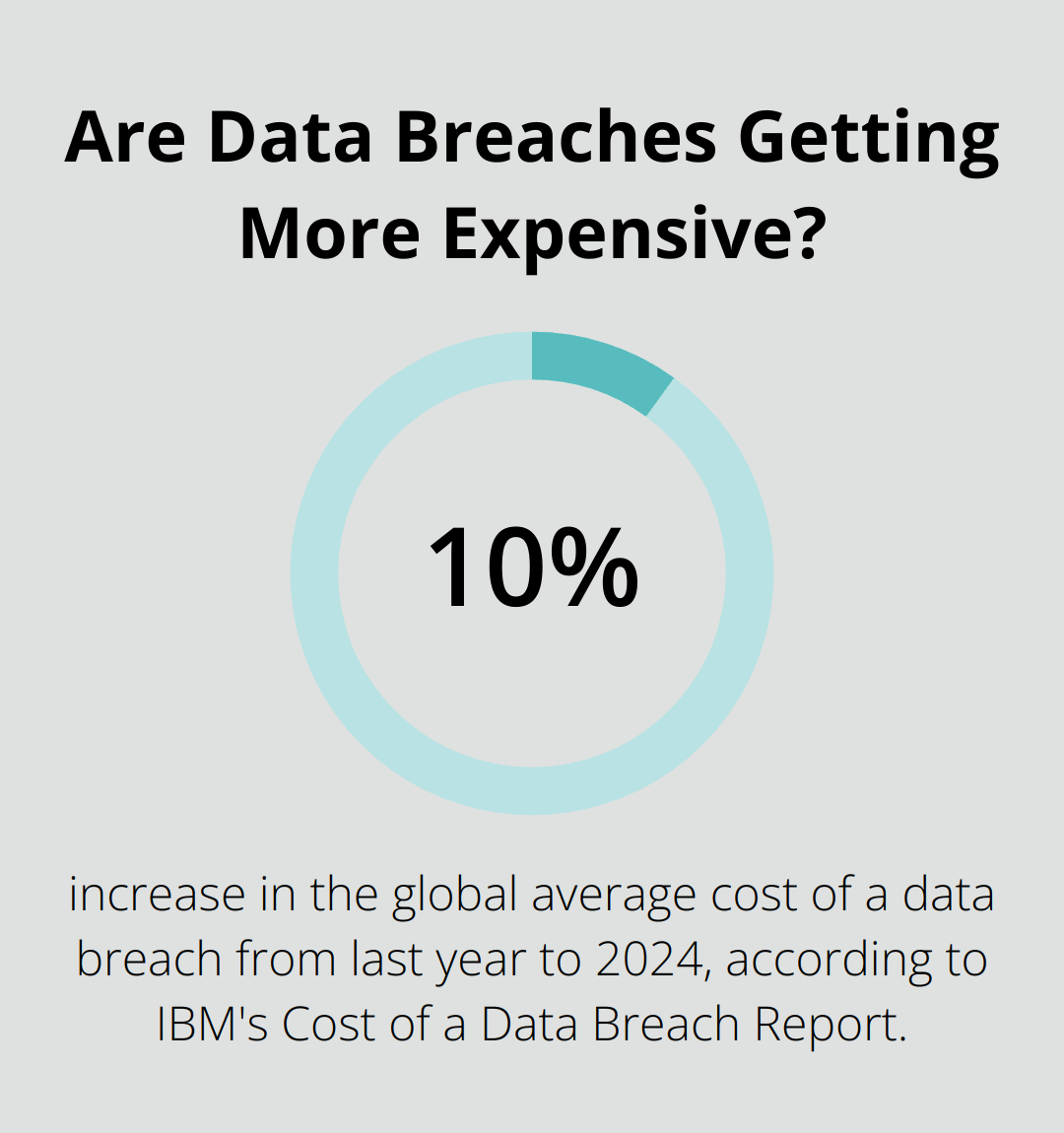
The High Stakes of Non-Compliance
Ignore at your peril… The HHS Office for Civil Rights could come knocking with fines from $100 to a jaw-dropping $50,000 per violation (or per record)-up to $1.5 million a year per slip-up. Case in point-Anthem Inc. shelled out a cool $16 million in 2018 for missteps affecting nearly 79 million folks.
Ongoing Vigilance: The Key to Compliance
HIPAA compliance? It’s not a checkmark, it’s a lifestyle. Developers have to:
- Keep risk assessments on repeat
- Stay in update mode for uncovering new holes
- Drill the staff on HIPAA essentials
- Be audit-ready, always
So, let’s dive into these core security measures that hold the line for HIPAA compliance in software development. They’ll help forge steadfast applications, keeping sensitive health data locked tighter than a drum-and uphold trust with healthcare pros and patients for life.
How to Implement Essential Security Measures for HIPAA Compliance
Let’s get into it-implementing solid security measures is the bedrock of HIPAA compliance. Developers need to weave key security elements into their healthcare apps to keep sensitive patient info locked down tight. This chapter dives into the must-have security measures for checking the HIPAA box.
Encryption: Your First Defense
Encryption is a must-have-no negotiating here-when it comes to shielding your electronic Protected Health Information (ePHI). The Security Rule lays out nationwide standards for protecting health info handled or bounced around in electronic form.
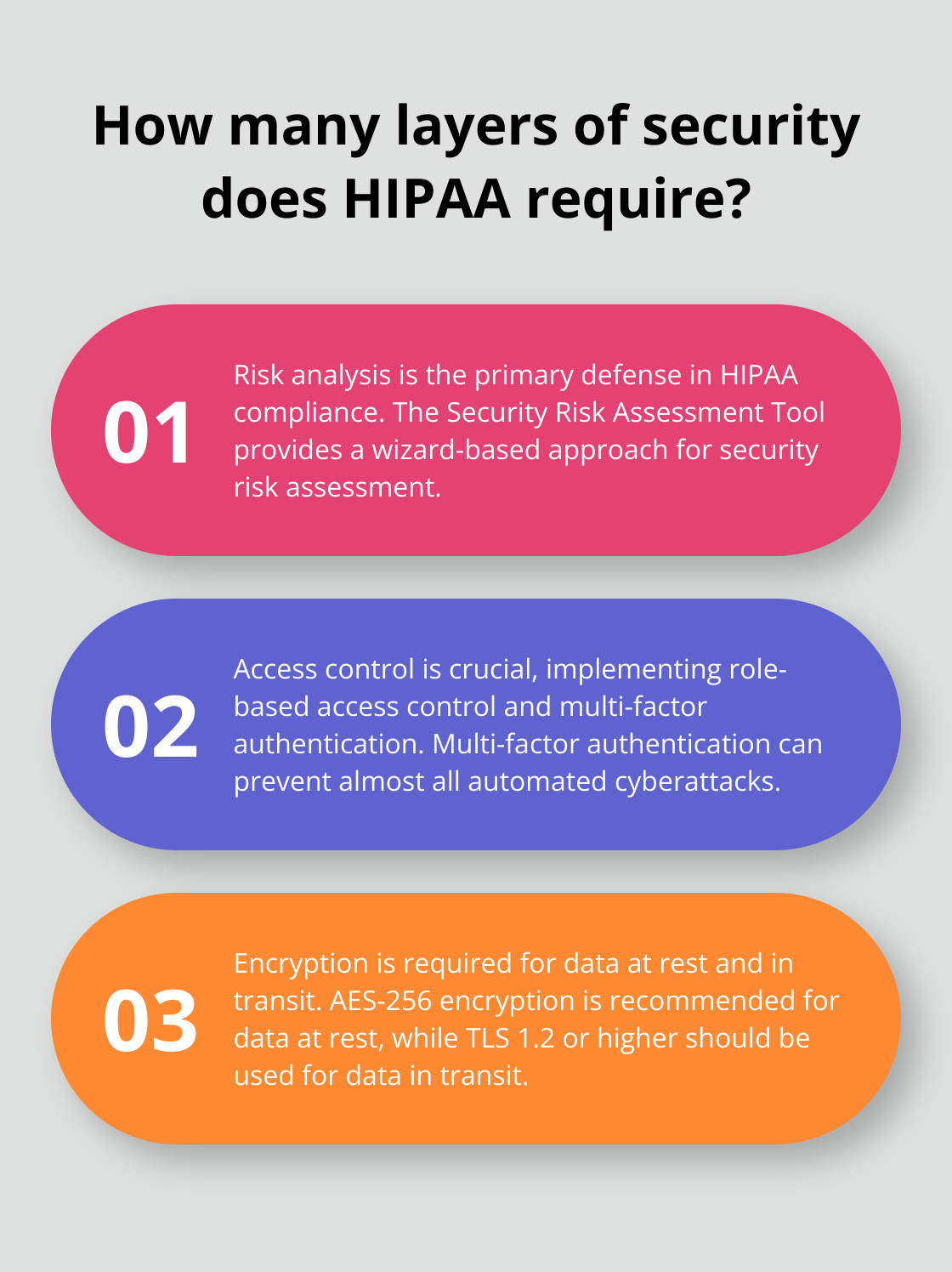
For your data chilling at rest, AES-256 bit encryption is the gold standard-seriously, the National Institute of Standards and Technology (NIST) backs this up, and it’s pretty much unbreakable with today’s tech tools.
When data is on the move, TLS 1.2 or going higher ensures everything whizzing between servers and clients stays encrypted-your defense against nosy eavesdroppers and sneaky tampering. And hey, keep those SSL/TLS certificates up-to-date to fend off any holes in your security armor.
Access Controls: Guarding the Gates
Role-based access control (RBAC) makes sure folks only access the info they need for work, lining up with HIPAA’s keep-it-minimal standard. This standard pushes healthcare groups to dial down the PHI use and disclosure to just what’s needed, no more, no less.
Layer on some multi-factor authentication (MFA) for every user account-you especially need it for those all-powerful admin accounts.
Autologoff after, say, 15 minutes of ghosting prevents unauthorized access if someone forgets to log out or dashes from their desk.
Audit Logs: Tracking Every Action
You need comprehensive audit logging to keep tabs on user doings-logins, data access, tweaks, and deletions. These logs should be rock solid and securely stored.
With a centralized log management system, you can round up and dissect logs from every system-easier monitoring and quicker red flags for any sketchy security happenings. Alerts for fishy behavior, like a barrage of failed login tries or odd data access moves, cranks up security another notch.
Backup and Recovery: Preparing for Emergencies
Lock in a strong backup game plan sticking to the 3-2-1 rule: three data copies, two backup copies on different storage rides, and one copy chilling offsite. Encrypt all backups, of course-they need to be secure even if physically breached.
Test those backup and recovery moves regularly. A full restore test each year tells you your backups have your back and your recovery process won’t flake out.
All these security moves not only tick the HIPAA compliance boxes but also beef up your security setup-protecting sensitive patient data and winning trust with healthcare clients. In the next chapter, we’ll dive into baking privacy into software design, kicking up that HIPAA compliance and user trust another notch.
How to Bake Privacy into Your Software Design
Prioritize Data Minimization
Alright, here’s the deal – privacy-first design kicks off by grabbing only the data you truly need. We’re talking “bare essentials” folks. This jives with HIPAA’s minimum necessary standard… and hey, less data equals less risk. So, ask yourself for every piece of info: Is this crucial for what we’re doing? Or, can we just as easily do without it?
Take a medical appointment scheduling app. Does it need someone’s entire medical saga? Nope. Stick to the basics: name, contact details, and appointment times. This makes privacy better (and bonus: it streamlines data management).
Create Granular User Controls
Give the people what they want – control over their own data. Craft interfaces that are so easy a toddler could navigate them to view, edit, or delete personal info. Standards like CCPA and GDPR are the new norm for user data rights. Healthcare apps need to step up and match-or beat-these.
Think about adding these features:
- A dashboard showing all the data collected about users
- The ability to download personal info in a machine-readable format
- One-click requests for data deletion
- Privacy settings that let users pick and choose what they share
Secure Third-Party Integrations
Listen, lots of healthcare apps bring in third-party services for extra stuff like payments or data analytics. Each hookup opens a door to possible vulnerabilities… so choose your partners with care.
When scoping out third-party services:
- Check for HIPAA compliance and their readiness to sign a BAA
- Look into their security practices and certifications (think SOC 2 Type II)
- Use API keys and tokens instead of passing around login credentials
- Encrypt any and all data transfers
Be upfront with users about who you’re bringing to the party and how data’s getting shared. Toss this info into your privacy policy and set up a page where users can easily find details about all data-sharing partners.
Implement Strong Authentication Measures
It’s not rocket science: solid authentication is a must for guarding sensitive health data. Get multi-factor authentication (MFA) in play for every user account, with extra attention on the admin ones. This throws another security blanket over just passwords and bolsters HIPAA compliance, locking down data, keeping patient info safe, and ensuring audit trails are spot on.
Think about biometric authentication (yeah, fingerprints or facial recognition) for mobile apps. It’s the sweet spot for security and user convenience.
Regular Privacy Impact Assessments
Do regular privacy impact assessments (PIAs) – think of it as your checkup for privacy risks. These spot risks and help curb them as they pop up. PIAs help you:
- Identify the types of data you collect and use
- Judge if your data processing is necessary and proportionate
- Weigh the risks to individuals’ rights and freedoms
- Put in measures to counter these risks
Remember, PIAs aren’t a one-and-done. They’re like flossing… gotta do ’em often. Do ’em any time new features roll out or whenever data processing practices take a turn.
Final Thoughts
HIPAA compliance-it’s not a one-and-done deal, folks. It’s a relentless game of whack-a-mole for those brave enough to develop software in the healthcare sector. Regular risk assessments? Yeah, they’re the unsung heroes here, exposing cracks before they become canyons. And let’s not forget employee training (because nothing says “I care” like a well-informed team) and that gloriously tedious documentation that makes auditors smile.
The healthcare field is like New York City-constantly shifting, never sleeping-meaning developers need to be on their toes, all the time, about HIPAA changes. A HIPAA compliance checklist? That’s your trusty roadmap, guiding you to create software that’s not just a check in a regulatory box, but genuinely secure, reliable, and capable of delivering meaningful benefits to both healthcare providers and patients.
At ScriberJoy, HIPAA compliance isn’t just a buzzword; it’s the backbone of our medical transcription software. We came here to build secure, precise documentation tools for healthcare, and to make life easier for the folks in scrubs. By keeping our products steadfastly compliant and secure, we let healthcare professionals zero in on what really matters-patient care.

Leave a Reply
You must be logged in to post a comment.