HIPAA compliance in cybersecurity is a critical concern for healthcare organizations. At ScriberJoy, we understand the complexities of protecting sensitive patient data while adhering to strict regulatory requirements.
This blog post explores the key considerations for maintaining HIPAA compliance in your cybersecurity strategy. We’ll cover essential measures, common challenges, and the benefits of robust security practices in healthcare.
Understanding HIPAA Compliance in Cybersecurity
The Essence of HIPAA
HIPAA, the Health Insurance Portability and Accountability Act, stands as a pillar of patient privacy protection in the United States. Enacted in 1996, HIPAA establishes national standards for safeguarding sensitive patient health information. Its impact on healthcare cybersecurity is profound and far-reaching.
The Security Rule: HIPAA’s Cybersecurity Foundation
The Security Rule forms the core of HIPAA’s cybersecurity requirements. This rule mandates that all covered entities and their business associates implement appropriate safeguards to protect electronic protected health information (ePHI). These safeguards fall into three categories:
- Administrative safeguards (e.g., risk assessments, employee training, incident response plans)
- Physical safeguards (e.g., controlling access to facilities and workstations)
- Technical safeguards (e.g., access controls, audit controls, transmission security)
The Growing Threat Landscape in Healthcare
The importance of robust cybersecurity in healthcare continues to escalate. The 2021 HIMSS Healthcare Cybersecurity Survey reveals that 67% of healthcare organizations experienced a significant security incident in the past 12 months. These incidents can result in devastating consequences, including patient data breaches, disrupted operations, and substantial fines.
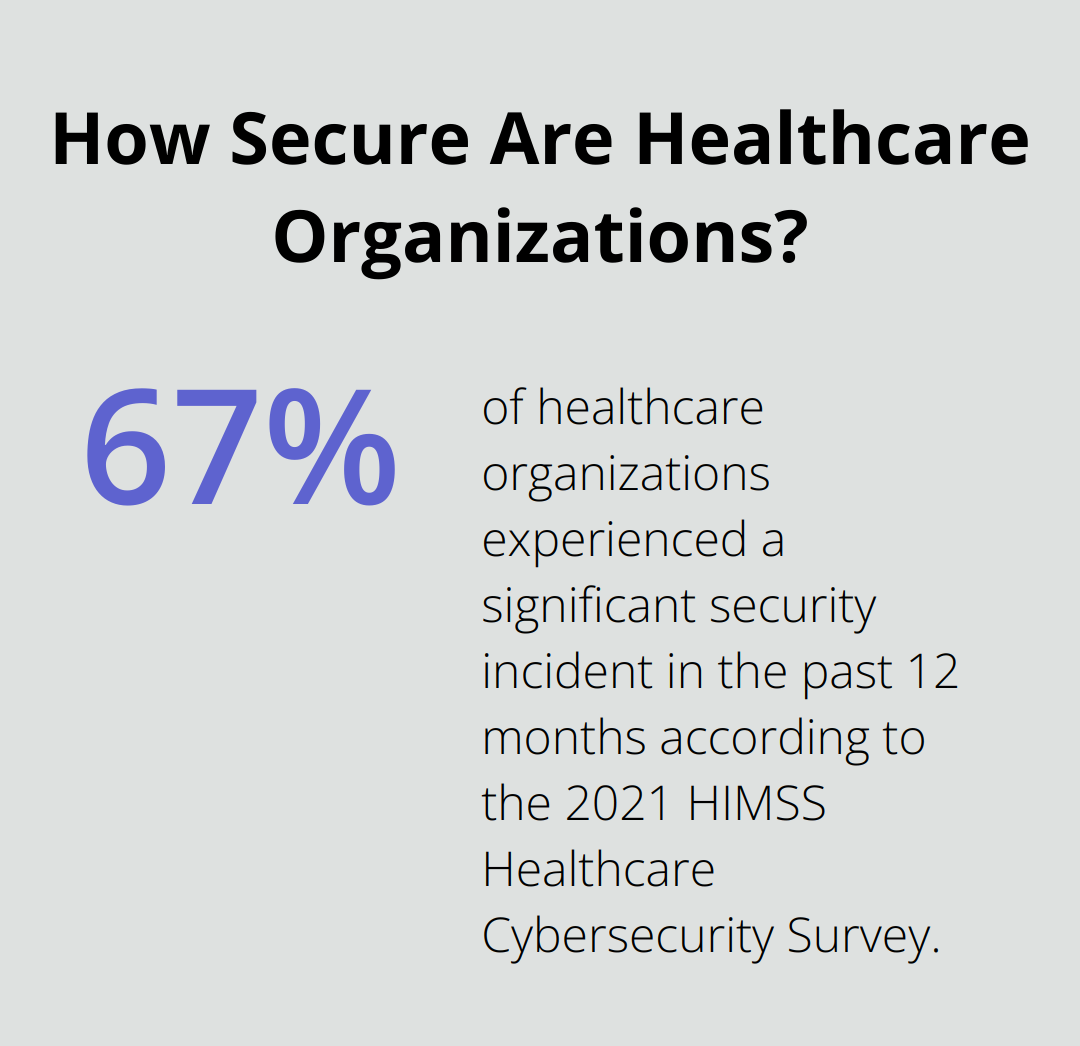
IBM’s Cost of a Data Breach Report for 2020 highlights that the average cost of a healthcare data breach reached $7.13 million. This figure significantly surpasses the global average across all industries, emphasizing the critical nature of healthcare data protection.
Practical Steps for HIPAA-Compliant Cybersecurity
Healthcare organizations must take concrete action to meet HIPAA requirements and protect against cyber threats. Key steps include:
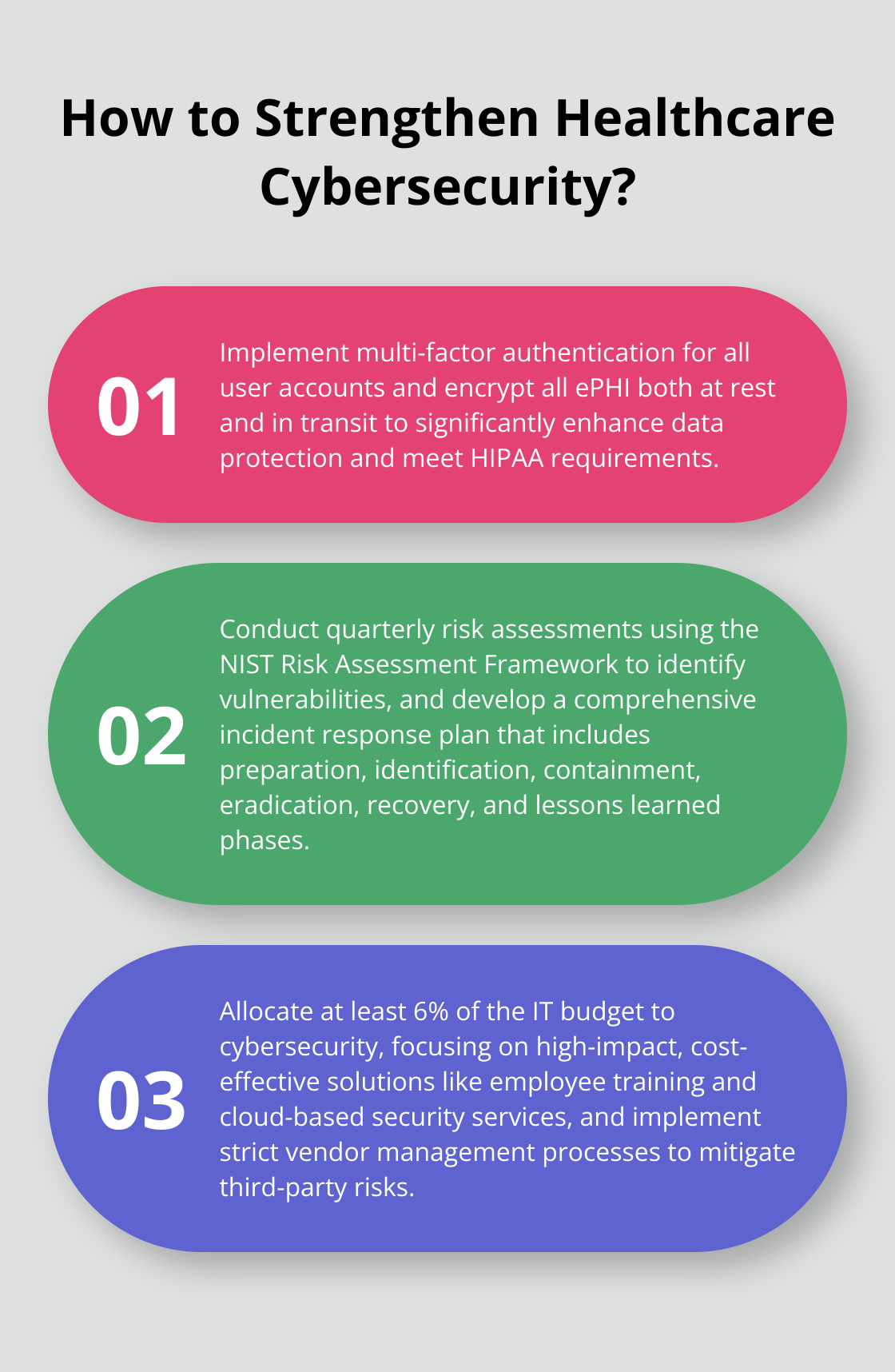
- Implement multi-factor authentication for all user accounts
- Encrypt all ePHI, both at rest and in transit
- Conduct regular security awareness training for all staff members (the Department of Health and Human Services recommends at least annual sessions, with more frequent updates for high-risk employees)
- Perform thorough and regular risk assessments to identify potential vulnerabilities in systems and processes
- Develop and maintain a robust incident response plan, outlining clear steps for detecting, reporting, and mitigating security incidents
It’s not enough to have these measures on paper – regular drills and simulations are necessary to ensure your team can execute them effectively when needed.
The Role of Technology in HIPAA Compliance
Advanced technologies play a significant role in maintaining HIPAA compliance. AI-powered tools can help detect anomalies and potential security breaches in real-time. Blockchain technology offers promising applications for secure health data management and sharing. Cloud-based solutions (when properly configured and secured) can provide scalable and cost-effective options for storing and processing ePHI.
As we move forward, we’ll explore the essential measures healthcare organizations must implement to ensure HIPAA compliance in their cybersecurity strategies.
How to Implement Essential HIPAA Compliance Measures
Conduct Thorough Risk Assessments
The foundation of HIPAA compliance rests on comprehensive risk assessments. The Department of Health and Human Services recommends organizations perform these assessments at least annually. However, many experts advocate for quarterly assessments to keep up with rapidly evolving threats.

A robust risk assessment includes:
- Identification of all systems and applications that handle ePHI
- Evaluation of current security measures
- Determination of potential vulnerabilities and threats
- Assessment of the likelihood and impact of potential breaches
- Development of a plan to address identified risks
The NIST Risk Assessment Framework provides a structured approach to this process.
Implement Strong Access Controls
Controlling access to ePHI is paramount. Multi-factor authentication (MFA) is no longer optional – it’s a necessity. You can help prevent some attacks by banning the use of bad passwords, blocking legacy authentication, and training employees on phishing.
Role-based access control (RBAC) serves as another key component. RBAC ensures employees only access information necessary for their job functions. This principle of least privilege significantly reduces the risk of internal data breaches.
Secure Data in Transit and at Rest
Encryption serves as your best defense against data breaches. The HIPAA Security Rule doesn’t mandate specific encryption methods, but it requires covered entities to implement a method to encrypt and decrypt ePHI.
For data in transit, use protocols like TLS 1.3 or IPsec. For data at rest, consider full-disk encryption and file-level encryption. The National Cyber Security Centre recommends AES-256 for symmetric encryption and RSA (2048-bit) for asymmetric encryption.
Implement Robust Audit Controls
Audit logs act as your eyes and ears in the digital realm. They help you detect unauthorized access attempts, track user activities, and demonstrate compliance during audits.
Implement a Security Information and Event Management (SIEM) system to centralize and analyze logs from all your systems. According to Gartner, organizations that deploy SIEM technology reduce the time to detect threats by an average of 12 days.
Develop a Comprehensive Incident Response Plan
Despite best efforts, breaches can still occur. A well-prepared incident response plan is essential. The SANS Institute recommends including these key elements in your plan:
- Preparation: Define roles and responsibilities
- Identification: Detect and analyze potential incidents
- Containment: Limit the damage of the incident
- Eradication: Remove the cause of the incident
- Recovery: Restore systems to normal operation
- Lessons Learned: Review and improve your processes
HIPAA requires covered entities to report breaches affecting 500 or more individuals within 60 days of discovery.
The implementation of these measures requires significant effort, but the cost of non-compliance far outweighs the investment. As we move forward, we’ll explore the common challenges organizations face in maintaining HIPAA compliance and how to overcome them.
Navigating HIPAA Compliance Hurdles
Resource Constraints and Budget Limitations
Healthcare organizations often face limited resources and tight budgets, which impede the implementation of comprehensive cybersecurity measures. A 2021 survey by the Healthcare Information and Management Systems Society (HIMSS) revealed that 59% of healthcare organizations allocate less than 6% of their IT budget to cybersecurity.
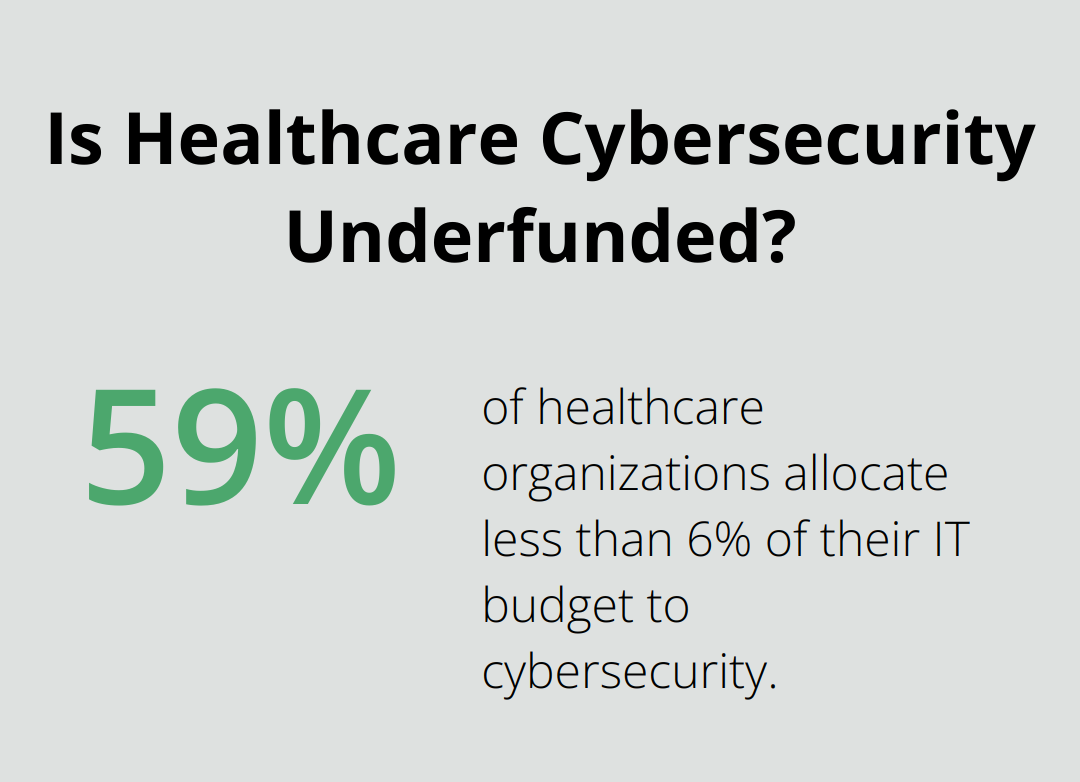
To overcome this challenge, organizations should prioritize their security investments based on risk assessments. They can focus on high-impact, cost-effective solutions like multi-factor authentication and employee training. Cloud-based security services offer advanced protection without significant upfront costs (and often provide scalability as organizations grow).
Keeping Pace with Evolving Cyber Threats
The cybersecurity landscape changes constantly, with new threats emerging regularly. The 2021 Verizon Data Breach Investigations Report highlighted that ransomware attacks in healthcare more than doubled in frequency from the previous year.
Healthcare organizations must adopt a proactive approach to threat intelligence. They should subscribe to cybersecurity feeds from reputable sources like the US-CERT and the Health Sector Cybersecurity Coordination Center (HC3). Regular updates and patches to systems address known vulnerabilities. AI-powered security tools can detect and respond to new threats in real-time (often faster than human analysts).
Effective Staff Training and Awareness
Human error remains a significant factor in data breaches.
Organizations should develop a comprehensive, ongoing training program that goes beyond annual compliance checks. They can use real-world scenarios and simulated phishing attacks to test and improve staff awareness. Creating a culture of security involves recognizing and rewarding employees who identify and report potential threats.
Managing Third-Party Vendors
Healthcare providers often work with numerous third-party vendors who may have access to sensitive patient data. This expands the potential attack surface and increases the risk of data breaches.
Organizations should implement strict vendor management processes. This includes thorough vetting of vendors’ security practices, regular audits, and clear contractual agreements regarding data protection. They should also limit vendor access to only the necessary data and systems.
Balancing Security with Usability
Stringent security measures can sometimes hinder workflow efficiency and user experience. Healthcare professionals need quick access to patient information, but this must be balanced with robust security protocols.
To address this, organizations can implement context-aware security measures. These adapt based on factors like user location, device, and access patterns. Single sign-on (SSO) solutions can also enhance both security and usability by reducing the number of passwords users need to remember while maintaining strong authentication.
Final Thoughts
HIPAA compliance in cybersecurity presents ongoing challenges for healthcare organizations. It demands a comprehensive strategy that includes risk assessments, access controls, data encryption, and incident response planning. The evolving nature of cyber threats requires healthcare providers to maintain constant vigilance and adapt their security measures regularly.
Strong HIPAA-compliant cybersecurity measures offer benefits beyond regulatory compliance. They enhance patient trust, protect organizational reputation, and improve operational efficiency. Healthcare providers who prioritize cybersecurity can focus on delivering quality patient care without the threat of data breaches or regulatory penalties.
At ScriberJoy, we recognize the importance of HIPAA compliance in healthcare technology. Our medical transcription software offers secure and accurate documentation solutions for healthcare providers. We help streamline the documentation process while maintaining high standards of data protection (leveraging AI technology with human verification).

Leave a Reply
You must be logged in to post a comment.